Sometimes it’s fun to turn the tables on the bad guys. A hobby of mine is hijacking botnets to see what all the fuss is about. The goal for today is to gain a shell on the malware host server.
DISCLAIMER: Don’t do any of this. It’s almost certainly illegal and jail sucks.
Anyway. C&C web panels are commonly included with malware, and act as a central dashboard providing statistics, command functionality, and access to stolen information such as passwords. As they are essentially the heart and brain of a malware campaign and can be used to control thousands of infected hosts they tend to be hidden on obscure domains, deep from the prying eyes of Google and other search indexers, making them difficult to discover. The panels themselves are usually secured with long and complicated passwords and sometimes require specific URL parameters to be present before access is granted.
They also tend to be poorly coded and subject to exploitation, which we will leverage to our advantage.
First, we need to find an admin panel for an active botnet. This can be difficult, depending on your standards, and often is time consuming. Options including reverse-engineering malware found in the wild, using a malware tracker, or social engineering someone on one of the underground forums. Because I’m lazy I chose option 2, using a malware tracker, which conveniently provides the C&C url directly. The downside is the link most likely will not last long now as it has been marked as a malware host. Most serious threat actors will migrate to a new domain at the first whiff of public detection.
 |
| Fig 1: malware tracker |
Looking at some recent URLs we see a domain hosting both KeyBase and Pony, making this ideal for reasons discussed shortly. Serious players almost never use a single host for multiple C&C panels, meaning the owner or owners are most likely new to the scene and inexperienced. This is good for us as it increases our chances at finding a bug or mistake to exploit.
As detailed by Paolo Stagno at VoidSec, the panel for KeyBase is rather poorly coded and has a couple of major vulnerabilities, including SQL injection. Here’s the vulnerable bit of code, located in file post.php:
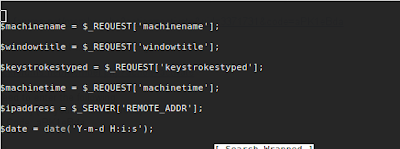 |
| Fig 2: post.php variable definitions |
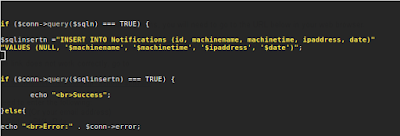 |
| Fig 3: vulnerable $sqlinsertn function |
Notice the utter lack of input validation – escaping the query and appending our own code at $machinename in figure 3 is what allows us to own this server.
Using sqlmap we can view the databases available to the mysql user. We also learn that the backend is Windows, and that we have db-admin privileges. We also can tell from the table names of the current db that a zeus or citadel panel is lurking somewhere on the server.
According to VoldSec the KeyBase application also has a file upload vulnerability. Unfortunately I was unable to get this to work, leaving us to find another way to access the backend system.
Now, due to design flaw or some other unknown reason, the creators of the Pony malware loader store the login credentials for the panel to the database itself…in plain text. Let’s take a look:
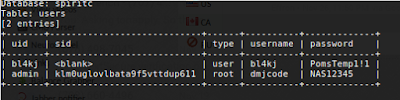 |
| Fig 4: Pony C&C panel users |
Now we have the admin credentials for one of the panels present: dmjcode/NAS12345
 |
| Fig 5: infected machines and stolen passwords |
 |
| Fig 6: Nope |
 |
| Fig 7: write errors on sqlmap |
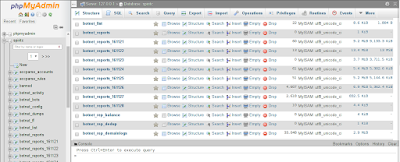 |
| Fig 9: Looking at some local databases |
 |
| Fig 10: Simple PHP backdoor. I chose a random table to add it to |
Closer view:
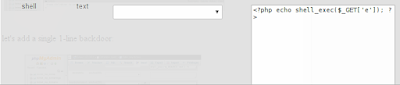 |
| Fig 11: Same |
Using the MySQL SELECT into outfile command, we can write to the local file system. Because this is Windows, we have permission to write to the local htdocs folder:
 |
| Fig 12: Writing the backdoor to the local file system |
Now we have a backdoor to the local windows machine.
 |
| Fig 13: Viewing the local file system |
Using a combination of local files and executing my own SQL statements, I was able to find the zeus panel and log myself in. The password was the same as with pony – don’t reuse passwords! Even bad guys make this mistake.
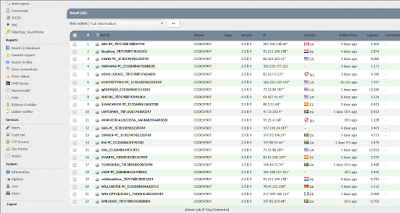 |
| Fig 14: Zeus family malware C&C panel. Not sure which one this is. |
Poking around on the zeus panel, it seemed some of the bots were pushing version of cryptolocker. Unfortunately I was not able to penetrate the host that controlled this software. The good news is that they were using a version of cryptolocker-type malware that Kaspersky has a tool to decrypt files.
Also on host were CC tracks and full card info for online and in-store fraudulent purchases.
 |
| Fig 15: CC info |
The owners of the malware caught on at this point and took everything offline. Unfortunately for them, all the bots not yet suffering from cryptolocker were deleted by me first 🙂

